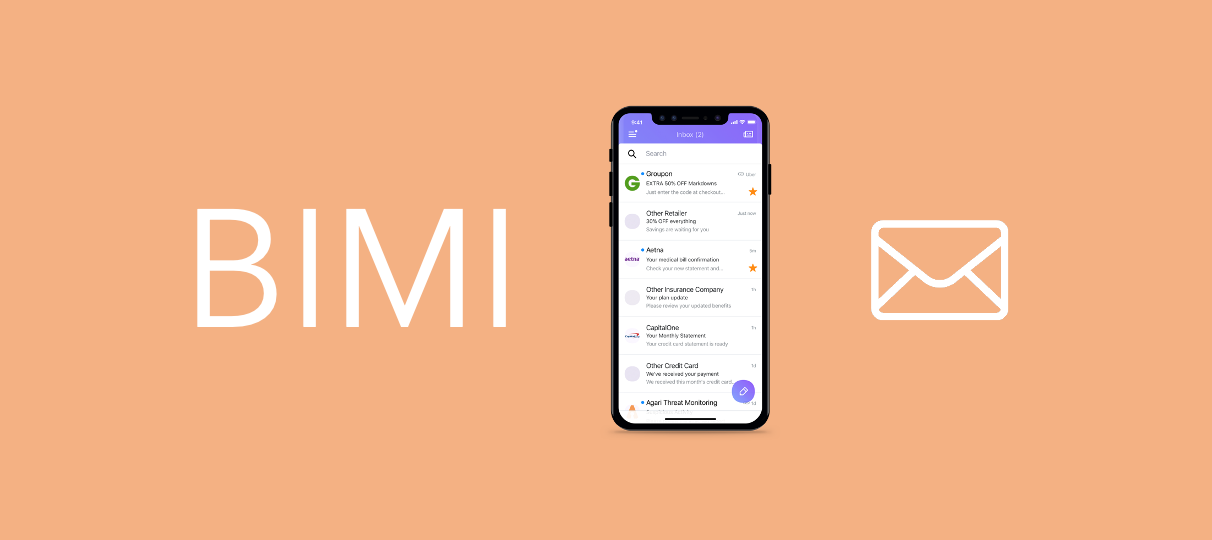
BIMI helps brands to communicate better and emails to be more secure Day after day, the battle for attention in the inbox is fought by a multitude of brands and senders. In the recipient’s inbox – wh...

BIMI helps brands to communicate better and emails to be more secure Day after day, the battle for attention in the inbox is fought by a multitude of brands and senders. In the recipient’s inbox – wh...

DKIM beyond authentication – Protecting Brand identity and reputation According to RFC 5863 the DKIM (DomainKeys Identified Mail) authentication allows an organization to claim responsibility for tr...
A good reputation, relevant content, and consistent list hygiene are the basis Resolutions belong to the New Year like fireworks and cava, but most of the time they remain what they are – just reso...

A good reputation, relevant content, and consistent list hygiene are the basis Resolutions belong to the New Year like fireworks and cava, but most of the time they remain what they are – just resolu...

It’s not always the case that everything runs smoothly on the Internet. Spam, phishing,Man-in-the-Middle attacks, spoofing; the list of sophisticated methods villains of theInternet utilize, is long. ...

Since its emergence, the email has established itself as a fast and uncomplicated communication medium. Alongside pure text, the email is also suitable for quickly exchanging small files like text doc...

DMARC stands for: Domain-based Message Authentication, Reporting and Conformance: domain-based message authentication, reporting and conformance of messages. The background to DMARC.org is to incre...