Sending quality marketing emails is about more than just a pretty design – and finding the right service provider is an important step ESPs are more than just senders Ever since the first electronic...
Search Results for: authentication
Whether a mailbox provider delivers an email to the inbox or classifies it as spam depends mainly on the reputation of a sender. Reputation is determined by a variety of factors. In this webinar, y...
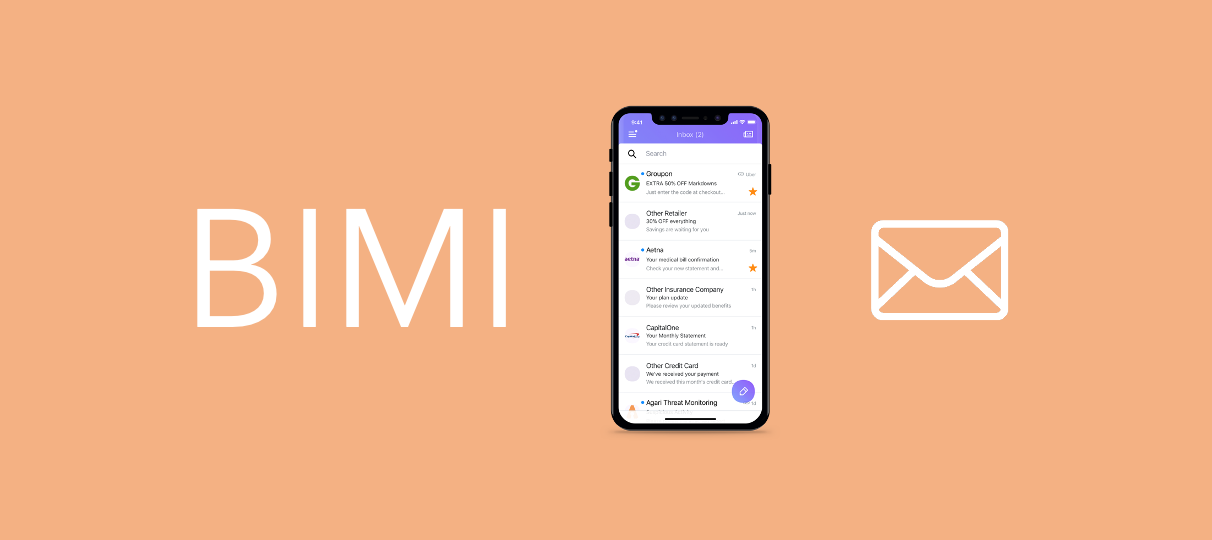
BIMI helps brands to communicate better and emails to be more secure Day after day, the battle for attention in the inbox is fought by a multitude of brands and senders. In the recipient’s inbox – wh...
We created the Smart Inbox as a way for users to spend less time managing their emails and more time focusing on the important things in life - which definitely shouldn't include organizing emails ...

What companies now have to consider when communicating by email with their customers Shops have closed, restaurants too, hotels are empty – the Corona pandemic has brought many regions to a virtual s...
One of the things I am working on at the moment is improving the speed at which Talos protects Cisco customers from new threats. Every second counts for zero-day or hailstorm attacks. If it takes 1...
A good reputation, relevant content, and consistent list hygiene are the basis Resolutions belong to the New Year like fireworks and cava, but most of the time they remain what they are – just reso...

A good reputation, relevant content, and consistent list hygiene are the basis Resolutions belong to the New Year like fireworks and cava, but most of the time they remain what they are – just resolu...

DMARC stands for: Domain-based Message Authentication, Reporting and Conformance: domain-based message authentication, reporting and conformance of messages. The background to DMARC.org is to incre...

DKIM is a widely used method for the authentication of emails. But when DKIM is not used correctly, it is not effective and can offer a false sense of security. For this reason, here we have summarize...