The workshop “Legal” covers the most important regulatory themes in relation to the sending of commercial emails, taking the current law and legal situation into account. Legalities and illegalitie...
Search Results for: ESP
The CSA Workshops allow your company to profit from the many years of experience of the Certified Senders Alliance (CSA) – a guarantee of quality for the highest technical and legal standards in Em...
The workshop “Deliverability” offers, as the name suggests, training in the technical and operative areas of Email Marketing. This workshop will provide you with an overview of the fundamentals and...
You are a Brand or an Email Service Provider and want to know the best practices in legal and technical standards or you simply have questions about certain issues? The CSA offers individual webina...
Email marketing is still one of the most successful and popular marketing tools. In addition to the technical standards, legal requirements must also be met. Since the new DSGVO, violations can res...
The header of an email contains important information, including the sender and the type of transfer path. The receiving mail server uses this information to decide whether it can trust an incoming...
Email clients render HTML codes of an email differently. Therefore, in addition to setting up an email header correctly, it is important that you also use a valid HMTL code in the body. In this web...
Whether a mailbox provider delivers an email to the inbox or classifies it as spam depends mainly on the reputation of a sender. Reputation is determined by a variety of factors. In this webinar, y...
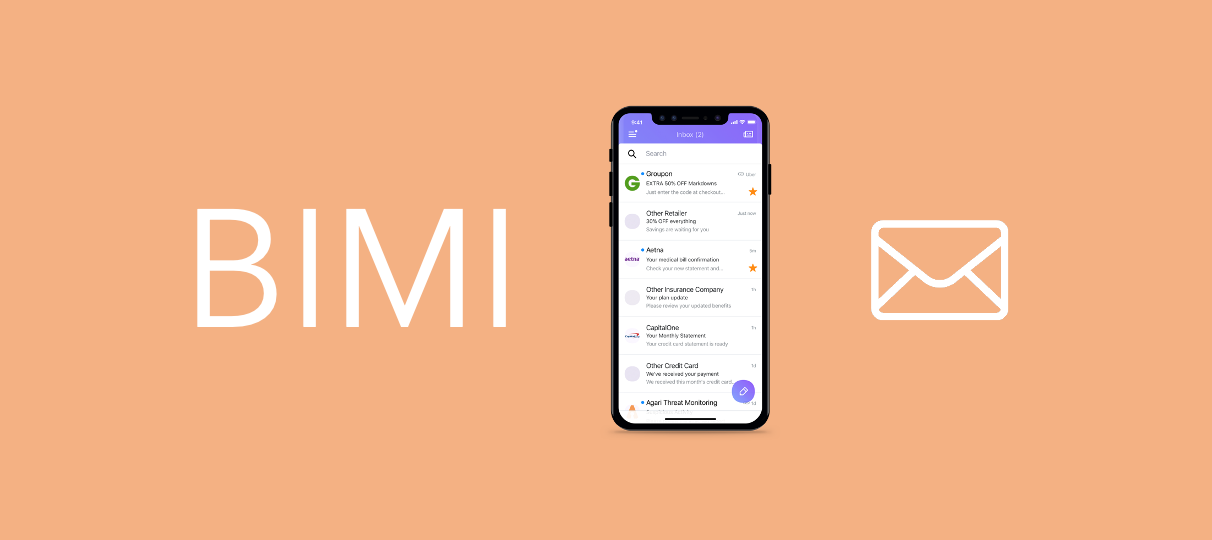
BIMI helps brands to communicate better and emails to be more secure Day after day, the battle for attention in the inbox is fought by a multitude of brands and senders. In the recipient’s inbox – wh...
We created the Smart Inbox as a way for users to spend less time managing their emails and more time focusing on the important things in life - which definitely shouldn't include organizing emails ...